Lately we have seen an increase in phishing email scams, with a lot of people unable to tell the difference between a legitimate email and a phishing scam, as cybercriminals are getting quite clever.
For those of you who don’t know what a phishing email is, phishing is the attempt to which cybercriminals send fraudulent emails containing website links requesting you to provide personal information such as passwords, passwords, credit card details.
About a year and a half ago, we released an article on how to spot scam emails, but it’s been getting harder for some to tell the difference between these emails, as cybercriminals will use logos to impersonate large companies and banks. To remind you, there are a few things you can usually spot in the emails. These are:
- Spelling and Grammar Mistakes: Spelling mistakes seem to be quite common for phishing scammers to make in their emails. Grammatical errors are also quite common, with some sentences not quite making as much sense as they would if they were coming from legitimate companies. However, a lot of people seem to skip past reading the email and just click the links as they see company logos in the email received.
- The URL: Websites that don’t display “https” in the URL bar aren’t secure. This means they don’t have a security certificate or SSL certificate. If you are visiting any website to fill out confidential online forms and/or provide payment details or login, you must make certain that the website displays “https” in the URL.
- Password or Login Requests: You receive unusual requests like password requests in the email, or requests to login to websites.
- Unusual Account Balances: You are alerted of unusual account balances in the email requesting payment, for example, a phishing email from an electricity company.
Can you usually tell a phishing email from the sender’s email address?
Unfortunately, sometimes you can’t. Not with the fact that people are using legitimate email addresses to send emails from and clever subdomains, which we will look into in the following examples.
#1 – The legitimate email address:
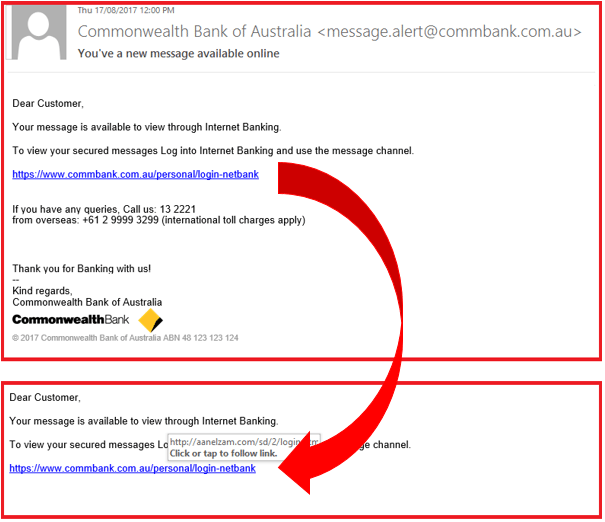
In this particular email, the cybercriminal who put this together did a great job at impersonating the Commonwealth bank. This is evident as: the email address is showing “commbank.com.au” in the domain name, the link in the email is showing as “commbank.com.au” on the surface and the email contains the Commonwealth Bank’s real 13 number.
One of the only ways to tell that this is a phishing email designed to get your attention is by hovering over the link included in the email which reveals another destination (“http://aanelz”) for the link rather than “commbank.com.au”, which shows on the surface of the email before hovering over the link.
A couple of other things we noticed in this email as well which stood out were:
- How they addressed the recipient by “Dear Customer”.
- The fact that they have put capital letters on “internet” and “banking” for no reason in the first sentence: “Your message is available to view through Internet Banking”.
- How they put a capital letter on “log” as well in the second sentence: “To view your secured messages Log into Internet Banking and use the message channel”.
- The way they used a capital again on “call” in the last paragraph “If you have any queries, Call us: 132221”.
The context of this email doesn’t make sense either. If you read closely into the grammar used in this email, legitimate companies when notifying you would normally start this email off with “A message is available”, not “Your message is available”, as it makes sense to do so.
#2 – The clever subdomain:
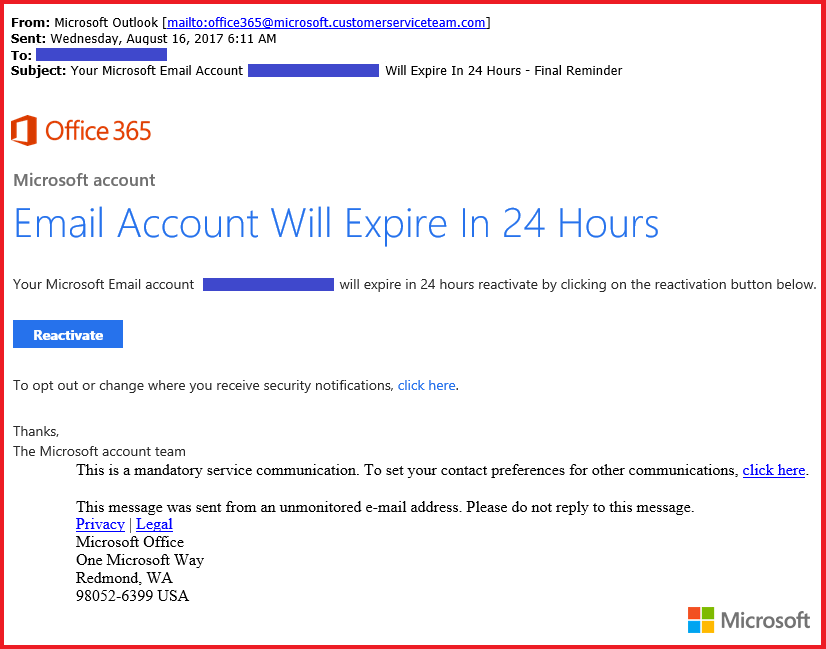
In this particular email, the cybercriminal has done a great job as well in making this look like it’s from Office 365, using a clever subdomain to send the email from.
To explain subdomains, it is basically a child domain name part of a parent domain name (ie: subdomain.parentdomain.com). The main (or parent) domain name comes after the sub domain (or child).
As an example, looking at our domain name, forerunner.com.au, if we had a subdomain name, it would look like “subdomain.forerunner.com.au”, so you can see in this example, “@microsoft.customerserviceteam.com” that the actual main domain name is “customerserviceteam.com”.
Now, knowing this, why would Microsoft email from a domain like this?
No, they wouldn’t email you from “customerserviceteam.com”!
If they were going to email you from a subdomain that contained the words “customerserviceteam”, the email address would be the opposite way around, as in: “@customerserviceteam.microsoft.com”, showing “microsoft.com” as the main domain name in the email address.
If you receive an email from a bank, service or company you are associated with, read the content of the email first and see if it makes sense to you, then hover over the links in the email to see where they really go. If the email doesn’t make sense to you in the first place, chances are it’s a phishing scam.
Contact us, if you’re ever unsure!







